Top of Page
- Links to move inside this page.
IIJ C-SOC Service
About the Service Overview
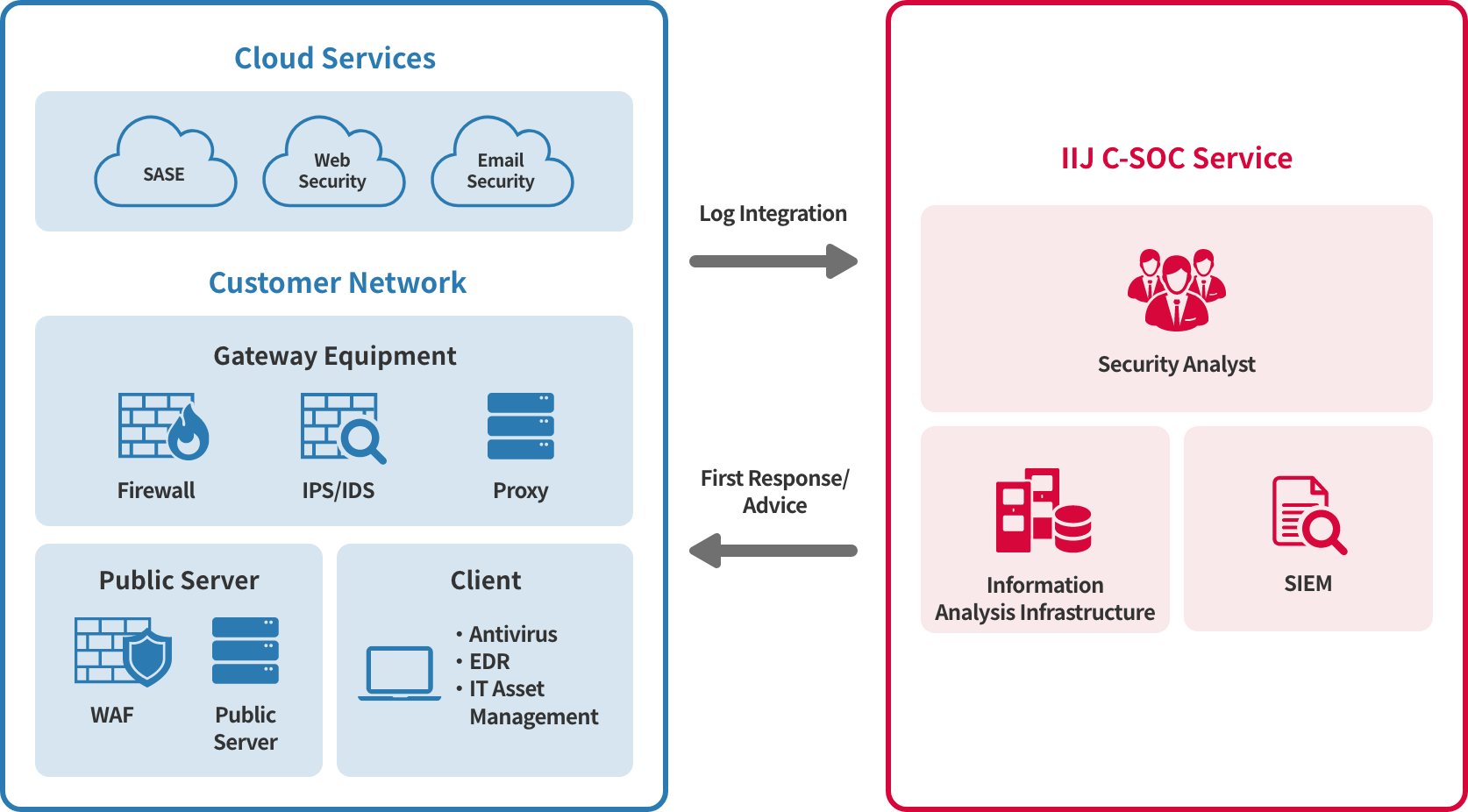
The IIJ C-SOC Service analyzes security logs collected from security devices and your operations equipment by using information analysis infrastructure and SIEM. This protects your environment from security incidents 24/7.
We beef up your security measures in ways that include suggesting countermeasures in response to incidents, and even changing the settings on IIJ-operated equipment.
Service Features
One-Stop Coverage from Equipment Operation to Incident Protection
This service provides total support from installation and operation of security equipment to log collection and analysis.
When incidents occur, IIJ will change the configurations of operated equipment as necessary to rapidly respond to serious attacks.
Early Threat Detection and Protection Using IIJ's Unique Knowledge
This service provides access to analysis logs and alerts from security equipment, as well as backbone traffic, DNS queries, and other external information.
This information is collected and analyzed by our information analysis infrastructure and SIEM to provide you with statistics, early detection of threats, and security configuration/policy suggestions.
Experienced Security Analysts
Since 1994, when it launched Japan's first firewall service, IIJ employs many security analysts experienced with protecting critical systems such as financial services, government systems, and e-commerce sites.
IIJ has the experience and track record to protect you from threats that become more sophisticated every day.
(Japanese text only)
- Related Contents
End of the page.