Top of Page
- Links to move inside this page.
IIJ Vulnerability Management Solution with yamory
About the Solution Overview
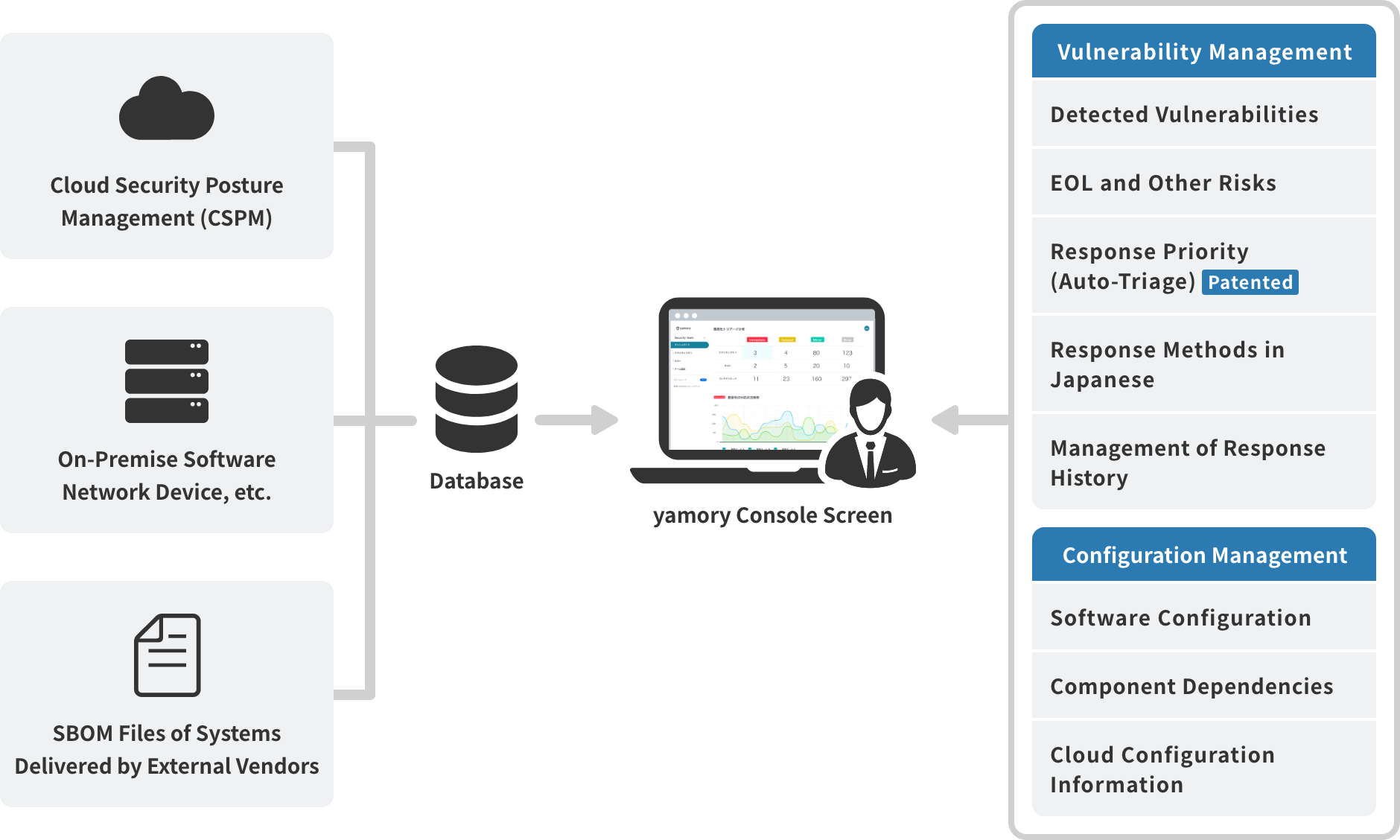
IIJ Vulnerability Management Solution with yamory automatically determines the order of priority for handling vulnerabilities based on which vulnerabilities have experienced actual attacks and three objective criteria: risk, impact, and attack method. This greatly reduces the workload of vulnerability management, which is a common challenge in daily operations.
Additionally, with configuration management, risks such as expired software licenses and cloud configuration deficits can be managed using our proprietary database.
* "yamory" is a vulnerability management cloud service provided by Assured Inc.
Solution Features
Automatic Prioritization of Protections, Reducing Workload
The system automatically prioritizes what to protect based on three objective criteria: the vulnerability score, accessibility from external sources, and the presence of attack code. This enables effective vulnerability management, even in the absence of security experts.
Broad Risk Management
This service not only manages vulnerabilities but also provides centralized management of various software-related risks through means that include product life cycle management, visualization of open source software license violations, and SBOM(*) support.
* Software Bill of Materials: A list of software components
Visualizing Diverse Assets and Implementing Centralized Management
This service supports a wide range of areas, including the cloud, on-premise, and software. This enables cross-departmental and cross-vendor management of products that are otherwise handled separately, all on a single platform.
(Japanese text only)
- Related Contents
End of the page.